TV : Jean s'est fait plaisir en mélant plusieurs techniques de stégano pour ce chall
First, let’s take a look at the file :

It’s a wav audio file with the generic of the media TF1, let’s see if there are some metadata in this file :
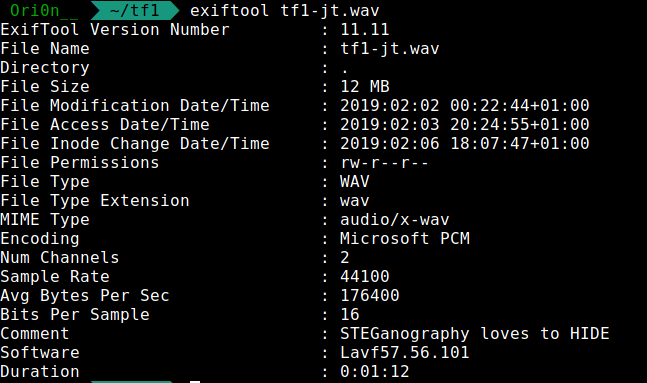
We have the comment “STEGanography loves to HIDE”, if we just take the letters in UPPERCASE we have the word STEGHIDE. Ok we will use steghide, and what about the password ?
The name of the event is HackSécuReims, and the format flag for every challenge is URCACTF{flag}, so let’s try with some words like this :
HackSécuReims
HackSecureims
HSR
hsr
URCACTF
urcactf
...
Use this command :
steghide extract -sf tf1-jt.wav
Result :

The password was URCACTF. If we analyse the file pass.txt we have a base64 string, so let’s decode it with this command :
cat pass.txt|base64 -d > file_pass_txt
If we take a look a the file :
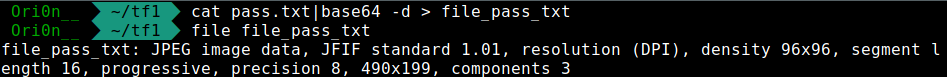
It’s a JPEG file, so open it :

We have some passwords written into a notepad. But what can I do with this ? Return to the wav file. We try the binwalk command in order to find some other file.
binwalk --dd=".*" tf1-jt.wav
Result:
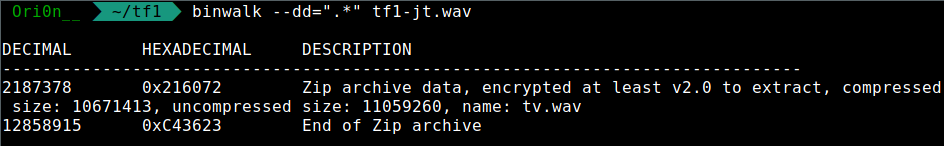
There is a ZIP archive who contain another wav whose name is tv.wav. Let’s try to unzip the file :
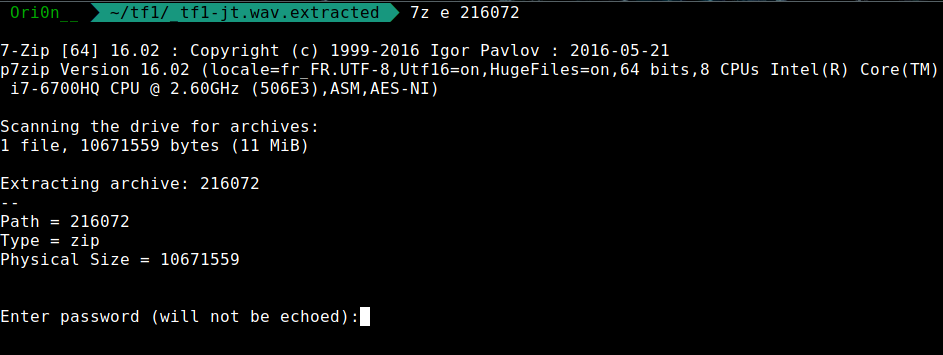
We have to find a password, so I’ll try the passwords that are written on the notepad found above :
My password
123456
qwerty
Re8!te3=
The password of the zip file was Re8!te3=. Let’s take a look at those new files :

It’s another wav, but if we listen carefully, seems like a minitel sound. After that, we remember about a ECW challenge : Link Here
So we put the sound into a Windows VM and run the sound with the tool RX-SSTV. And we can view the flag :
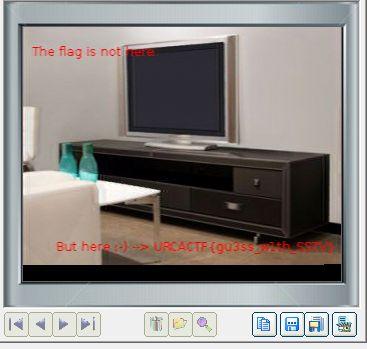
Flag : URCACTF{gu3ss_w1th_SSTV}
