March
4th,
2019
First, let’s take a look at the file :
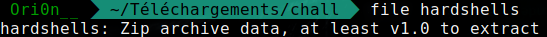
It’s a Zip archive, so try to unzip it :

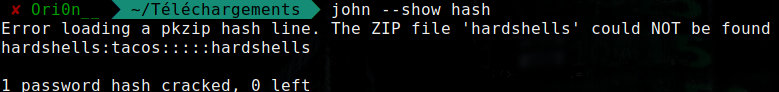
We need a password, I used john to crack it :
zip2john hardshells > hash
john hash
And we got the password :
Now we have a Minix file whose name “d”, mount it :
mount -t minix d /mnt/test
And we have a new file “dat”, if we look at the header with hexdump we suppose it’s a .PNG but the header has been modified :

Use a hexeditor to modified the U(55 in hex) to N(4e in hex)

Now you can open it and read the flag :
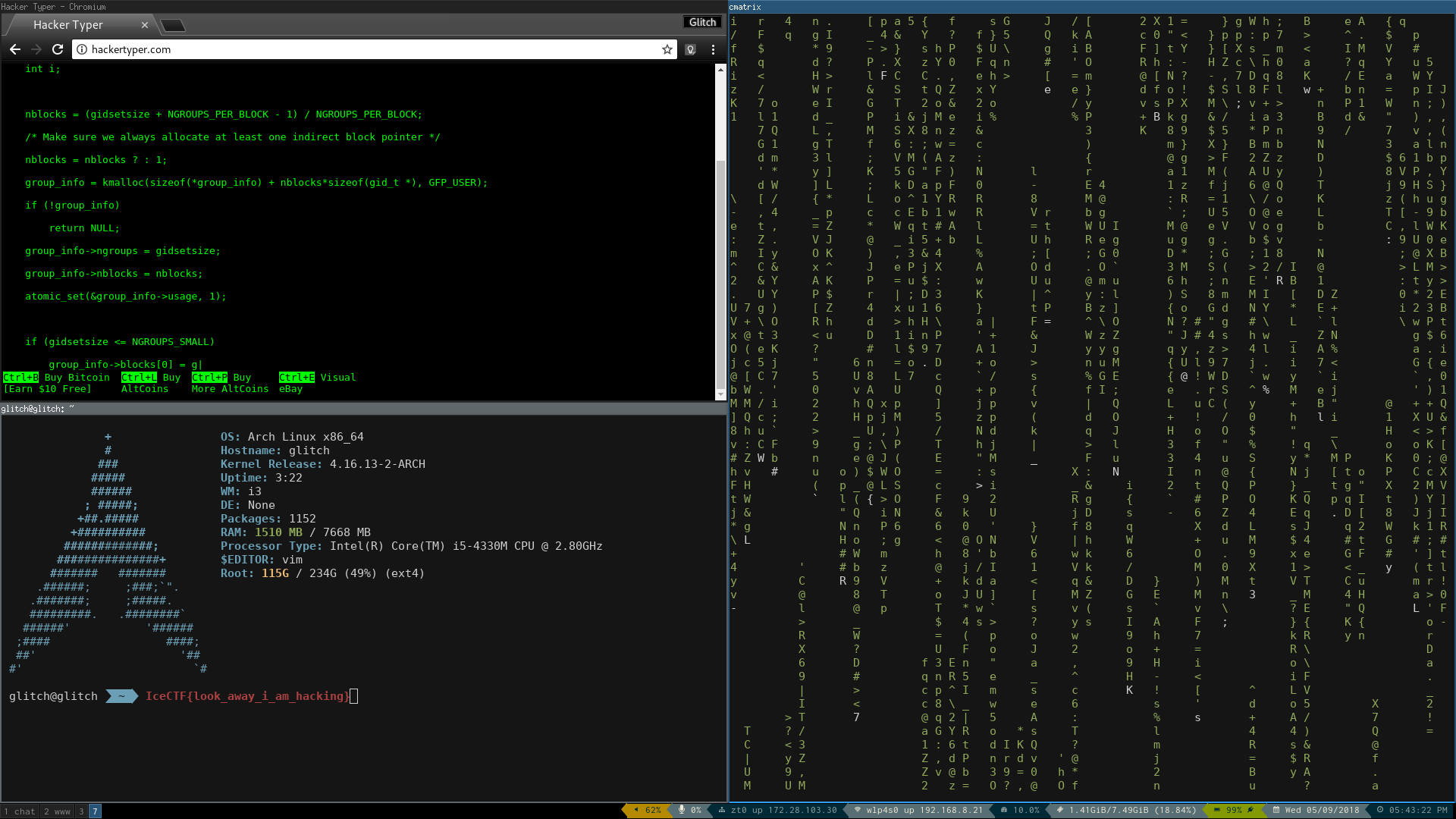
Flag :
IceCTF{look_away_i_am_hacking}
