March
8th,
2019
First let’s take a look at the file :

It’s a picture, I used stegsolve,zsteg, exiftool on it but nothing interesting. So I tried binwalk, and I’ve got some results :
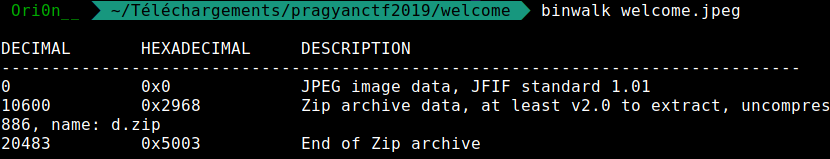
The picture contain a zip file, let’s extract it :
binwalk --dd=".*" welcome.jpeg
The zip file contain another zip d.zip
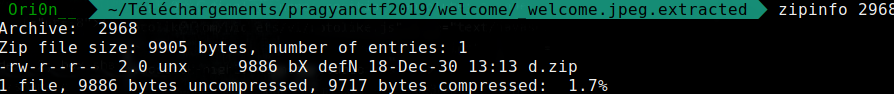
Let’s extract the new zip, and now I have 2 files a.zip and secret.bmp. I tried to unzip the zip but it’s asking for a password, so I focus on the secret.bmp. I took a look at the files to see what it contains :
okdq09i39jkc-evw.;[23760o-keqayiuhxnk42092jokdspb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!@pb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!?@&{:keqay^IFG{wfdoiajwlnh[8-7.=p54.b=dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==
There is some base64, let’s try to decode it :
Python 2.7.15 (default, Jan 10 2019, 23:20:52)
[GCC 8.2.1 20181127] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> print "dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==".decode("base64")
the password is: h3110_th3r3!
>>>
So now I have a password, maybe for the zip. I tried it and this was the good one for this zip. I have another picture :
Using stegsolve on it :
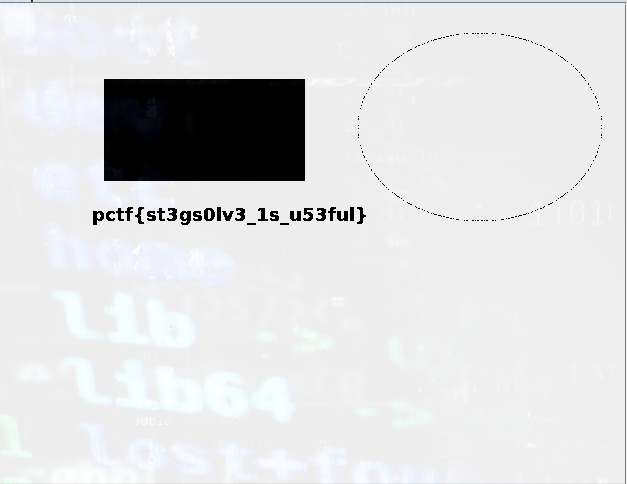
Flag :
pctf{st3gs0lv3_1s_u53ful}
