Login 1 :
Take a look the source code that was gives to us :
var http = require('http');
const crypto = require('crypto');
var url = require('url');
var fs = require('fs');
var _0x86d1=["\x68\x65\x78","\x72\x61\x6E\x64\x6F\x6D\x42\x79\x74\x65\x73"];
function generatePart1() {
return
{
x: crypto[_0x86d1[1]](8)
}[x].toString(_0x86d1[0]);
}
function generatePart2() {
return [+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]];
}
http.createServer(function (req, res) {
res.writeHead(200, {'Content-Type': 'text/html'});
passwd = generatePart1() + generatePart2();
var url_content = url.parse(req.url, true);
if (passwd == url_content.query.passwd) {
res.write(fs.readFileSync('flag.txt', 'utf8'));
} else {
res.write('<html><body><form method="get"><input type="text" name="passwd" value="password"><input type="submit" value="login" /></form></body></html>');
}
res.end();
}).listen(8888);
Go to an node.js online compiler like Link :
Copy/paste the code source and add the following line at the end :
console.log(generatePart1() + generatePart2());
Run it & you will see the password :

Let’s flag this :

Login 2 :
Take a look to the source code that was gives to us and you can see it’s a php loose comparison with a md5 hash.
if (hash("md5", $_GET['passwd']) == '0e514198428367523082236389979035')
So, submit a magic hash (240610708)Link to the password form and let’s flag this.

Login 3 :
Take a look to the source code that was gives to us and you can see, it’s a Flask Web App with Python. A detail in the code is very important. More precisely at the “main” part.
if __name__ == '__main__':
assert(len(passwd) == 3)
assert(passwd.isdigit())
app.run()
The password has a strict length of 3 characters and it’s only digit.
So, let’s fuzz the password with wfuzz and a list of all combination of 3 digits for a password.
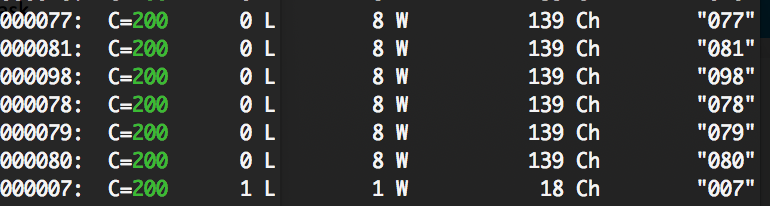
The password is 007 because wfuzz not have same number of characters of an error message.
Let’s flag this.
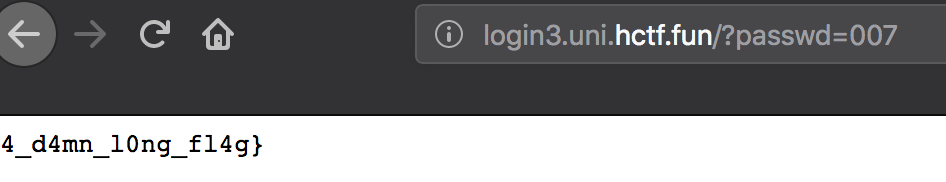
Flag :
flag{W0w_1_gu3ss_th1s_t0_be_4_pr3tty_4_d4mn_10ng_fl4g}
