March
5th,
2019

As we can see in the description, the file is a memory dump. And we have to find info.
First, let’s try to determinate the profile of this dump with volatility :
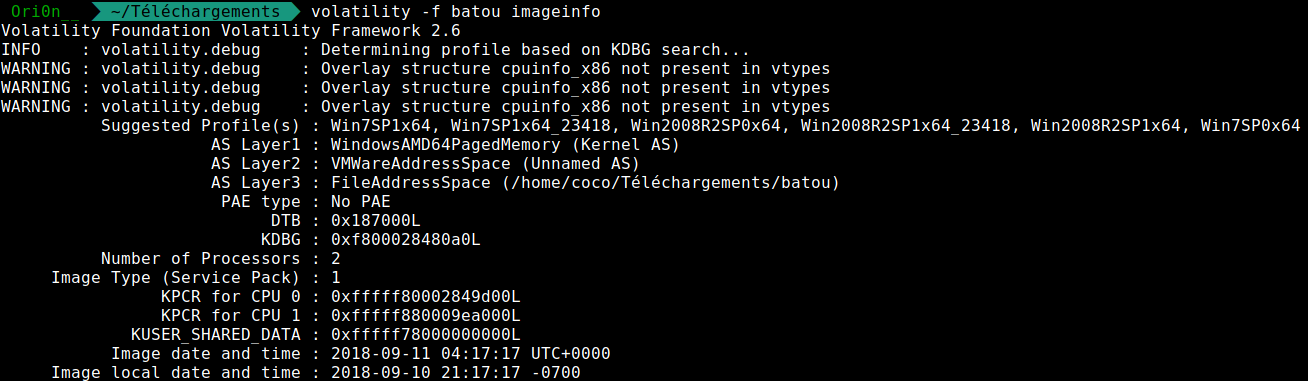
It’s a windows 7 !
Now let’s try to view some programs running :
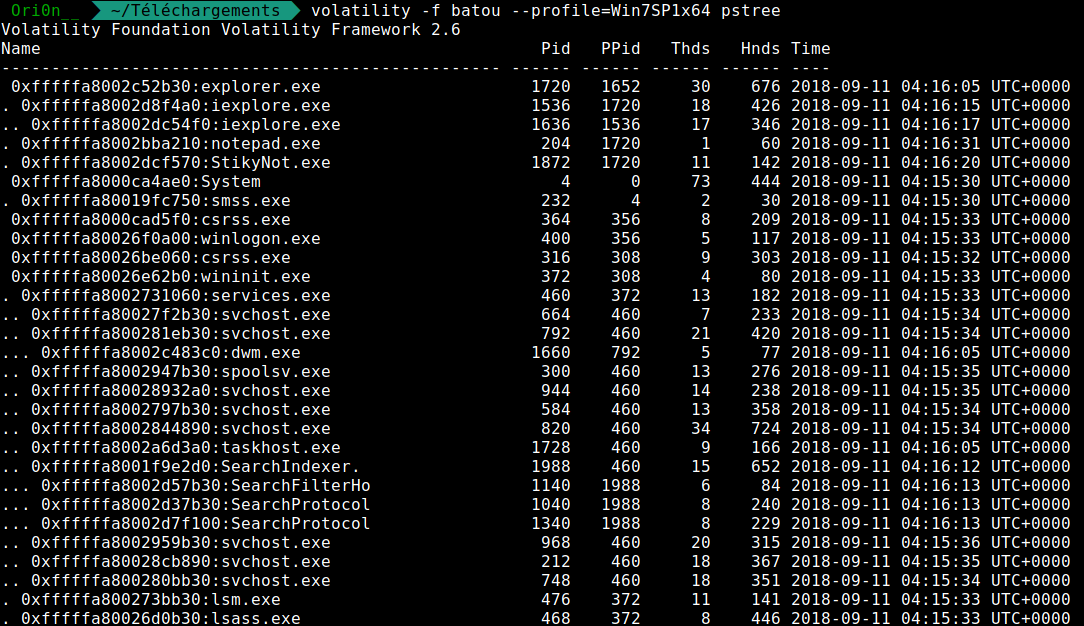
As we can see notepad.exe is running. So let’s see if they are some files running with notepad :
volatility -f batou --profile=Win7SP1x64 filescan|grep -ai Notepad
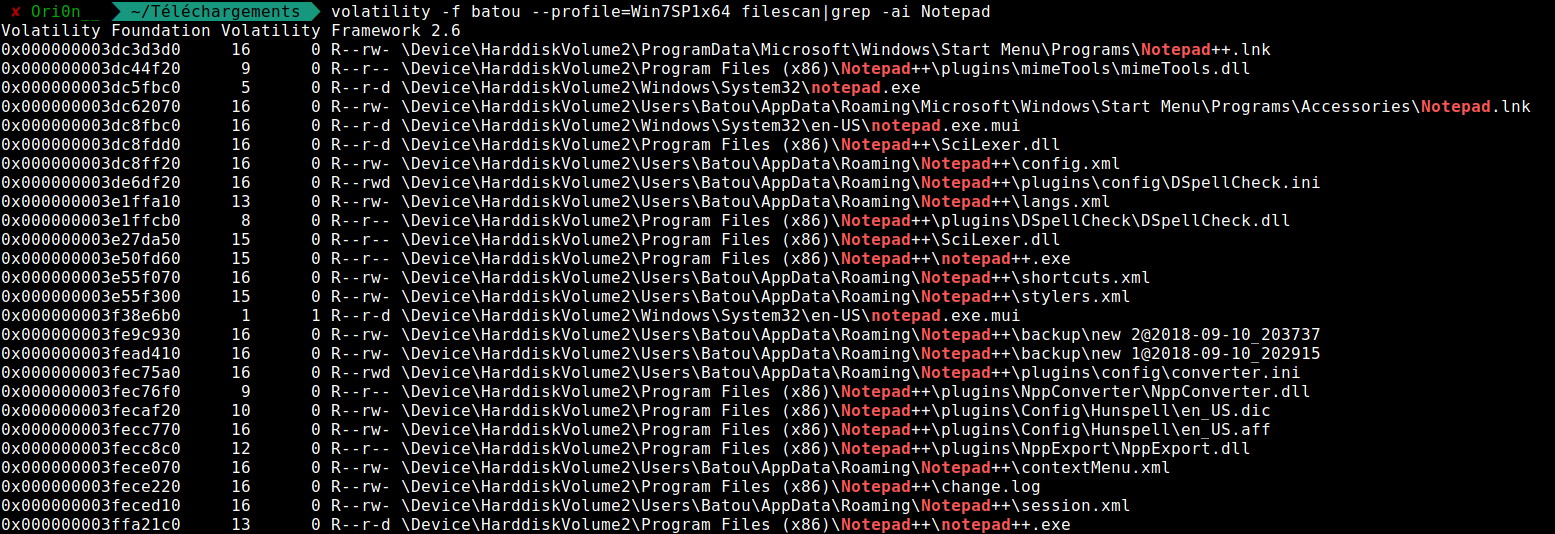
In 0x000000003fead410 and *** 930 they are 2 files, let’s try to dump them :
volatility -f batou --profile=Win7SP1x64 dumpfiles -Q 0x000000003fead410 --dump-dir .
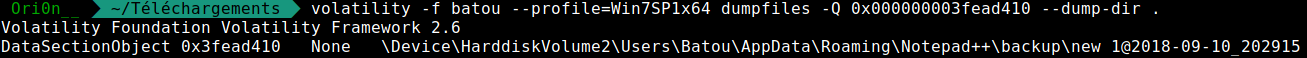
The 930 file is empty but the 410 contain that :

Seems like hex values, let’s decode them :
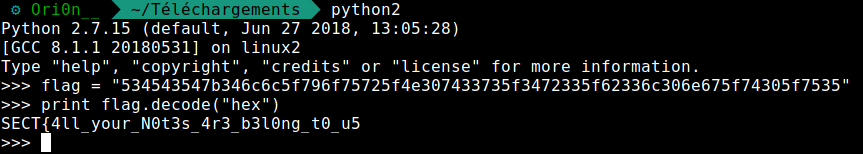
And we got the flag, I justed add the ‘}’ who was missing :
Flag :
SECT{4ll_your_N0t3s_4r3_b3l0ng_t0_u5}
